Azure account and Azure subscriptions
Azure account is used to establish a billing relationship. An Azure account is a user identity, one or more Azure subscriptions, and an associated set of Azure resources. The person who creates the account is the Account Administrator for all subscriptions created in that account. That person is also the default Service Administrator for the subscription.
Azure subscriptions help you organize access to Azure resources. They also help you control how resource usage is reported, billed, and paid for. Each subscription can have a different billing and payment setup, so you can have different subscriptions and different plans by office, department, project, and so on. Every service belongs to a subscription, and the subscription ID may be required for programmatic operations.
Each subscription is associated with a Microsoft Entra directory. To find the directory the subscription is associated with, open Subscriptions in the Azure portal and then select a subscription to see the directory.
Classic subscription administrator roles
The Azure platform offers three traditional subscription administrative roles, namely Account Administrator, Service Administrator, and Co-Administrator. These roles grant comprehensive access to an Azure subscription, allowing administrators to oversee resources through various means, including the Azure portal, Azure Resource Manager APIs, and classic deployment model APIs.
When an Azure account is initially created, it is automatically designated as both the Account Administrator and the Service Administrator. Additional individuals can be designated as Co-Administrators to share administrative responsibilities. Notably, the Service Administrator and Co-Administrators possess privileges comparable to those of users assigned to the Owner role, a role within Azure designated at the subscription level.
To illustrate, the following table outlines the distinctions among these three traditional subscription administrative roles.
In the Azure portal, you can manage Co-Administrators or view the Service Administrator by using the Classic administrators tab.
Azure role-based access control (Azure RBAC)
Azure RBAC is an authorization system built on Azure Resource Manager that provides fine-grained access management to Azure resources.Azure RBAC includes over 70 built-in roles. There are four fundamental Azure roles. The first three apply to all resource types:
The rest of the built-in roles allow management of specific Azure resources.
In the Azure portal, role assignments using Azure RBAC appear on the Access control (IAM) page. This page can be found throughout the portal, such as management groups, subscriptions, resource groups, and various resources.

When you click the Roles tab, you'll see the list of built-in and custom roles.

What can I do with Azure RBAC?
Here are some examples of what you can do with Azure RBAC:
✅ Allow one user to manage virtual machines in a subscription and another user to manage virtual networks
✅ Allow a DBA group to manage SQL databases in a subscription
✅ Allow a user to manage all resources in a resource group, such as virtual machines, websites, and subnets
✅ Allow an application to access all resources in a resource group
↗️How Azure RBAC works
A role assignment consists of three elements: security principal, role definition, and scope.
Security principal
A security principal is an object that represents a user, group, service principal, or managed identity that is requesting access to Azure resources. You can assign a role to any of these security principals.
Role definition
A role definition is a collection of permissions. It's typically just called a role. A role definition lists the actions that can be performed, such as read, write, and delete. Roles can be high-level, like owner, or specific, like virtual machine reader.
Scope
Scope is the set of resources that the access applies to. When you assign a role, you can further limit the actions allowed by defining a scope. This is helpful if you want to make someone a Website Contributor, but only for one resource group.
In Azure, you can specify a scope at four levels: management group, subscription, resource group, or resource. Scopes are structured in a parent-child relationship. You can assign roles at any of these levels of scope.
↗️Where is Azure RBAC data stored?
Role definitions, role assignments, and deny assignments are stored globally to ensure that you have access to your resources regardless of the region you created the resource.
When a role assignment or any other Azure RBAC data is deleted, the data is globally deleted. Principals that had access to a resource via Azure RBAC data will lose their access.
Microsoft Entra roles
Microsoft Entra roles are used to manage Microsoft Entra resources in a directory such as create or edit users, assign administrative roles to others, reset user passwords, manage user licenses, and manage domains. The following table describes a few of the more important Microsoft Entra roles.
In the Azure portal, you can see the list of Microsoft Entra roles on the Roles and administrators page. For a list of all the Microsoft Entra roles, see Administrator role permissions in Microsoft Entra ID.

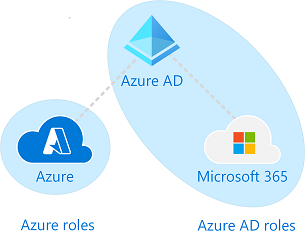
Differences between Azure roles and Microsoft Entra roles
At a high level, Azure roles control permissions to manage Azure resources, while Microsoft Entra roles control permissions to manage Microsoft Entra resources. The following table compares some of the differences.
More Details Read Ms Official Doc↗️
Comments (0)
Categories
Recent posts

AI (Artificial Intelligence) in digital ...
18 Dec 2023
Digital Marketing 2024 : Top 25 Digital ...
7 Dec 2023
A Beginner's Guide to Embarking on Your ...
5 Sep 2023
Quickstart: How to Create a Linux ...
6 Sep 2023CALL NOW ! +91 9037376960
100% Money-Back Guarantee: Invest in Your Success Risk-Free!



